- Articles
- We just avoided a Phishing attack (and you ca...
Table of Contents
When discussing cybersecurity with companies, we are often asked about phishing attacks and how successful they are. Phishing attacks are cyberattacks carried out against businesses by sending emails that install malware/ransomware/spyware on the victim’s computer if a malicious attachment is opened or a link in the email is clicked.
In our previous blog post “Phishing for Corporate Gold with Social Engineering Attacks” we got into the details about how to recognize and avoid phishing. In this blog we look at a real (and unsuccessful) phishing attack against Amaxra and look at just how successful this particular attack may have been against other businesses.
How successful are phishing attacks on businesses? The short answer: Very
So successful, that phishing by email is probably the most common way attackers target businesses. Because it really works.
Let’s look at a real-world phishing example and see who clicked. Just after 9 a.m. on August 30, 2017, an Amaxra employee received the following email:
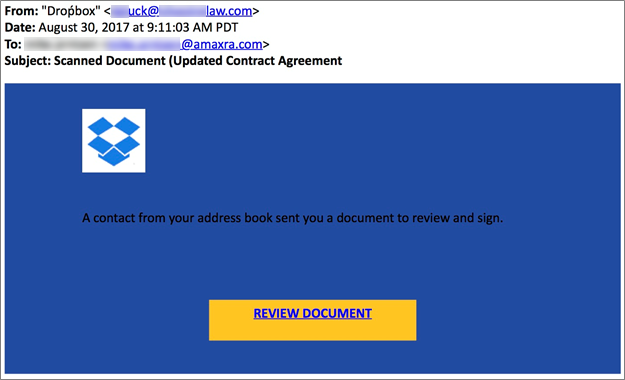
Note that we’ve blurred out the identity of our employee and the forged email address of the sender.
The email claims to be from “Droṕbox” (note the misspelling of well-known cloud storage provider, Dropbox, with an accent over the “p”). While the identified sender appears to be an employee of a well-known U.S. law firm.
This combination of a mis-matched sender name from an email address of a firm that Amaxra doesn’t do business with is a key indicator that this is a phishing email.
The link in the big yellow button you are invited to click isn’t a Dropbox URL. Hovering the mouse cursor over the button reveals a shortened bitly URL: “bitly.com/xxxxxxx“. We aren’t going to show you the URL because it leads to very real malware.
Because the button’s URL does not reference dropbox.com (which it should), it is another red flag that this email is a phishing attempt. Fortunately, the Amaxra employee saw the signs and did not click.
Finding out who did fall for this phishing email
Attackers usually send a phishing email to many different companies, trying to find anyone who will click. Since our attackers used Bitly.com to shorten and hide the URL of their malware, we can find out how many people clicked on the link, and when.
Like most URL shorteners, Bitly.com allows anyone to see how many people clicked on a shortened URL. You just type the shortened URL into your browser and add a “+” sign after it like this:
https://bitly.url/xxxxxxx+
Using the Bitly.com public analytics, we checked the click statistics of the phishing email’s URL just an hour after we first received it at Amaxra:
It looks like Amaxra was one of the first to receive this phishing email. The first clicks on the URL happened between 3 p.m. and 4 p.m. UTC (between 9 and 10 a.m. at Amaxra).
Notice that in the first hour of the attack, about 500 victims clicked on the link. That means the attack may have successfully penetrated the defenses of over 500 computers via this one phishing email.
Here’s the click-through statistics 12 hours later:
Notice the number of clicks reduces throughout the day. Most phishing attacks get immediate results that fall off as each hour goes by. Twelve hours after the initial attack, the total number of click-throughs on the URL is less than double the number of clicks in the first hour.
Shortened URLs are convenient but you don’t really know where they might lead your browser to. If you want to see where a shortened URLs points to, try using one of the expander services like http://www.checkshorturl.com.
I have anti-malware software, so my company is safe… right?
One of the problems today is that malware is often engineered to evade anti-virus and anti-malware solutions. Google offers a service called VirusTotal that allows you to upload suspected malicious attachments and URLs for scanning by more than 60 different anti-malware solutions.
Let’s see what https://VirusTotal.com says about the URL our phishing email presented:
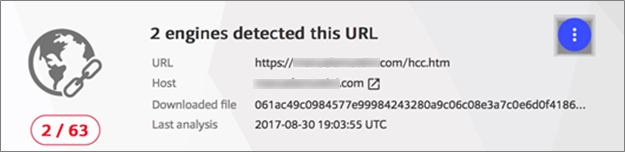
Notice that only two of the 63 scanners aggregated currently by VirusTotal identified the URL as suspicious. This is surprisingly common. Each anti-malware software solution uses a somewhat different approach to finding malware. Many of these anti-malware solutions use a set of rules to recognize and block malware on your computer. However, the malware developers understand the rules and are pretty good at evading detection by most anti-malware software solutions. While you should always have an anti-malware solution, your particular choice may or may not protect you.
Since each anti-malware solution continuously updates itself to detect new malware variants, within a few days most of the solutions will identify the specimen URL as pointing to malware and block it. But that won’t protect you if you click the URL in the phishing email in the first hour or the first day you receive it.
Employee training is the best solution to recognize phishing
Most malware today can evade detection by anti-malware solutions – at least for a few hours or a few days. Once malware takes hold of your computer, you may not know it’s there for months – and all that time if could be watching your every move. The malware could be stealing your valuable confidential corporate information or encrypting and locking you out of your files if it’s ransomware.
If you received the phishing email Amaxra received, and you knew the signs to look for, you too would have been able to prevent becoming a phishing victim. While malware can get past your software defenses, most people with just a bit of training can recognize malware quickly and avoid it.
Take 10 minutes out of your day to read our previous blog on recognizing phishing.
Want to have in-depth analysis of your company’s current IT security? Our cybersecurity experts will work with you to craft strategies for protecting your business against malware and other malicious attacks.
