- Articles
- Practical Guide to Windows Defender Advanced ...
Table of Contents
If you’re worried about cybersecurity, you have good reason.
It is no secret that the number of cyberattacks on business networks is increasing in number, but the threat becomes even more real when ransomware attacks start becoming more sophisticated.
- It takes a company 200 days to detect a security breach, and 80 days to contain it.
- Ransomware was 57x more destructive in 2021 than it was in 2015.
- The average cost of a data breach to a small business can range from $120,000 to $1.24 million.
What happens when even your antivirus solution can’t save you from advanced threats? How do you protect your network and ensure that you don’t fall prey to attackers – and even if you do, how can you make sure you bounce back quickly?
Windows Defender Advanced Threat Protection is a post-breach solution that works continuously to monitor your network, alert you in case of a breach, and also guide your next steps.
(If you like the sound of this, you’re going to like the rest of this article even more.)
What is Windows Defender Advanced Threat Protection
Windows Defender Advanced Threat Protection (now rebranded as Microsoft Defender for Endpoint) is a post-breach solution that detects, investigates, and responds to security threats on your network. Microsoft Defender for Endpoint keeps your network secure by continuously evaluating and identifying existing weaknesses in your system, addressing security concerns, and investigating security attacks that take place.
It is important to note that Microsoft Defender for Endpoint is not an anti-virus product (and cannot be substituted for one), but a post-breach solution that complements the capabilities of anti-virus solutions. Microsoft Defender for Endpoint is designed to help you after your network security has been breached.
So, if Microsoft Defender for Endpoint is not going to actively stop threats from entering your network, why exactly does it do and why do you need it?
Valid question.
Security threats are becoming increasingly complex and sophisticated, which means that no antivirus solution is iron-clad. The smart thing to do is to assume that a breach is going to occur, and equip yourself to be well prepared when it does.
When a breach does occur, Microsoft Defender for Endpoint will be there to:
- Tell you what the threat is and how it got in.
- Isolate and deal with the threat before it spreads and causes any further damage to your network.
- Update your Microsoft antivirus products with learnings about the behavior of that malware or attacker.
When you are not dealing with a security breach, it will be there to:
- Continuously detect and identify vulnerabilities in your system in real-time.
- Alert you in case of any suspicious activity.
- Provide you with remedial measures.
Windows Defender Advanced Threat Protection detects malware that has already made it past your antivirus software and alerts you immediately. Once you know there has been a breach, it helps you investigate and analyze the attack so you can decide what needs to be done to remediate it.
If the technology sounds too advanced to be true, remember that Microsoft constantly runs machine learning, AI, and big data analytics across its global ecosystem. Microsoft security teams translate these insights to enable Windows Defender for Endpoint to identify attacker tools, techniques, and procedures and generate alerts accordingly.
Windows Advanced Threat Protection Features & Capabilities
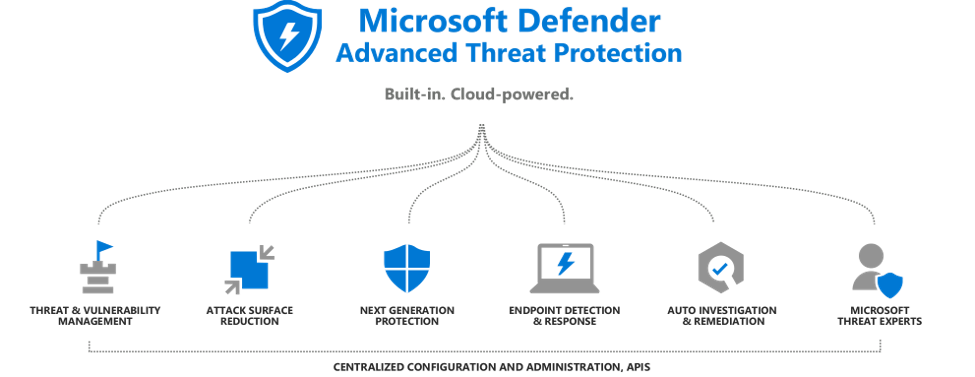
When we say Windows Defender for Endpoint is a holistic post-breach solution, we mean it’ll help you with all your threat detection, prevention, and remediation needs – even those you didn’t know you had.
It does this through its robust set of functionalities and capabilities designed to give you that extra layer of protection you need.
1. Threat and vulnerability management
Windows Advanced Threat Protection consistently performs real-time analysis on endpoints. It retains visibility over all software in a device. It is constantly working on identifying and assessing any security vulnerabilities that might exist in any of the applications on your device.
Only 47% of organizations monitor their networks 24/7. But what can you do to be part of the other, more prepared, 53%?
With Windows Defender Advanced Threat Protection, you can see your overall exposure score, vulnerable software and machines in your network, and what you can do to remediate the issues.
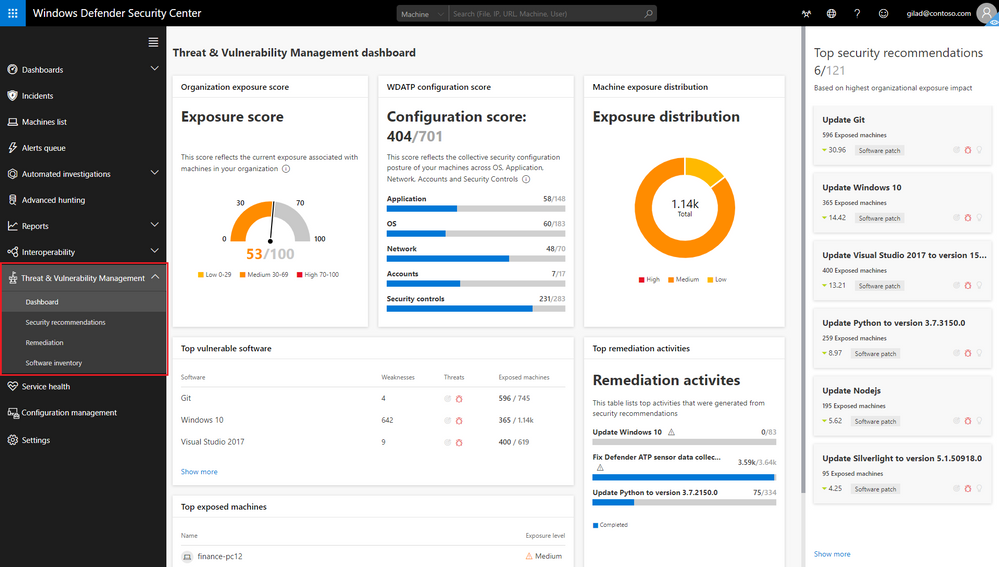
When it discovers any weakness or vulnerability in any device, it promptly alerts you and provides recommendations to remediate it.
2. Attack surface reduction
You can reduce the risk of a potential threat by minimizing areas where cyberattacks can take place.
This can be done through various controls put in place by Windows Defender for Endpoint, such as only allowing applications marked as ‘trusted’ to run on the device, allowing you to restrict certain behaviors in files and applications, as well as preventing untrusted websites, applications and files from accessing all areas in the device.
3. Next generation protection
78% of larger organizations say their information security function is only partially meeting their needs. Meanwhile, proactive cybercriminals continue to raise their game.
Windows Defender for Endpoint leverages Microsoft’s sophisticated technology and ongoing research in machine learning and threat resistance to provide you with behavior-based antivirus protection, cloud-delivered blocking, and constant product updates.
Rest assured, your network won’t be infected because your security system was too outdated or slow.
4. Endpoint detection and response
Being a post-breach solution, Windows Defender Advanced Threat Protection offers endpoint detection and response (EDR) capabilities that identify and warn you about suspicious activities.
Once suspicious activity is detected in your network, you will immediately be alerted and provided with data to investigate the threat and make an informed decision about your next steps.
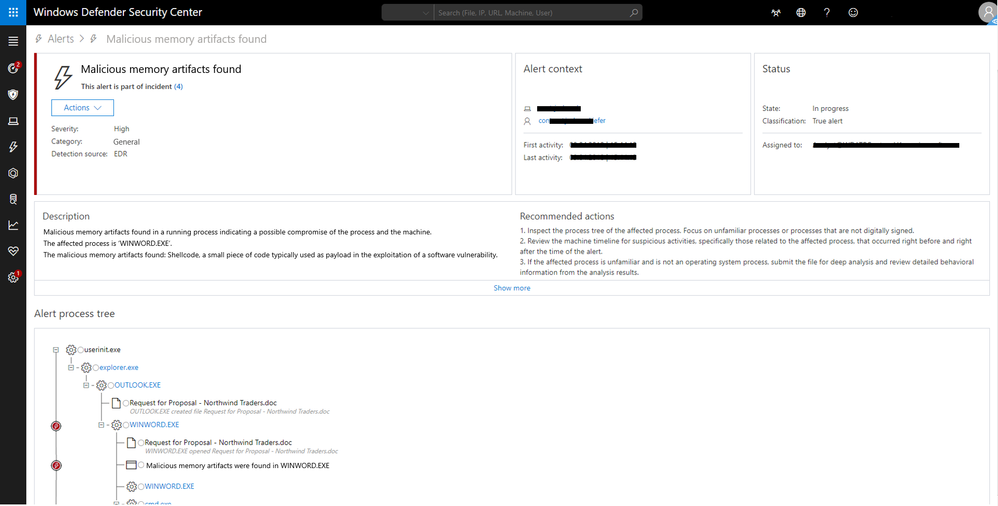
The Defender for Endpoint dashboard gives you access to in-depth data and analysis of different aspects of your security system from a centralized portal.
The endpoint detection and response in Windows Defender for Endpoint primarily consist of the following features and capabilities:
- Alerts: When a threat is detected, you will instantly receive an alert in your dashboard, along with basic information such as what the threat is, which device it has been found in, how severe it is, etc.
- Investigation: Your security team can investigate the threat further through features such as a timeline of events, which gives you a complete history of the threat since it arrived in your system, along with the list of machines that it has infected.
- Remediation: You will also be provided with a set of recommended next steps based on the behavior of the threat, and you can choose which action you would like to take.
Considering that companies that contained a breach in less than 30 days saved more than $1 million compared to those that took more than 30 days, investing in this feature might just be profitable.
5. Automated investigation and remediation
If you want to reduce the pressure on your IT team or ensure that nothing gets missed out, you can choose to rely on the automated service included with Windows Defender for Endpoint. Not just that, the average cost of a data breach can come down by more than 50% if the disaster recovery process is automated.
This means that some alerts will be remediated automatically so that your security team can focus on high-priority issues.
6. Microsoft Secure Score for devices
This feature allows you to assess the health of your network and identify devices that might be unprotected or prone to threat. While you may be consistently monitoring your network, human error remains the primary cause of 95% of cybersecurity breaches.
Preventing a security breach on one device, if done in time, can mean protecting your entire enterprise network from malware and viruses spread through device communication.
7. Microsoft threat experts
If you relate to any of the following problems faced by organizations around the world, you’ll appreciate this feature even more:
- More than 77% of organizations do not have a Cyber Security Incident Response plan.
- 45% say that their processes are ineffective at mitigating attacks.
- 43% of cyber attacks are aimed at small businesses, but only 14% are prepared to defend themselves.
Microsoft’s managed hunting services offer some extra help to your security team through two components:
- Targeted attack notification: Along with generating alerts for detected threats, you will receive special insights and analyses, meaning you can respond to high-priority threats quickly and without any mistakes!
- Experts on demand: When you’re feeling really lost or intimidated, you can reach out to Microsoft’s experts, who will provide you with technical consultation on how you can approach the problem.
These are just some of the extensive set of features provided by Microsoft Defender for Endpoint – there are many more micro ways in which it allows you to prevent, detect, investigate and remediate cybersecurity threats.
Defender Advanced Threat Protection’s holistic set of features and capabilities are designed to leave no stone unturned when it comes to equipping you with all that you need for detecting, investigating, and responding to advanced threats.
Advanced Threat Protection Plan 1 vs Plan 2

The benefits of Windows Advanced Threat Protection are available to you in two plans (which have now been renamed):
- Defender for Endpoint Plan 1
- Defender for Endpoint Plan 2
You can choose which one would suit you best based on the set of features and capabilities your organization requires for its safety needs. Let’s take a quick look at what’s included in the two plans:
| Capabilities | Plan 1 | Plan 2 |
| Next Generation Protection | Yes | Yes |
| Manual Response Actions | Yes | Yes |
| Attack Surface Reduction | Yes | Yes |
| Centralized configuration and management | Yes | Yes |
| Support for Windows 10, iOS, Android OS, and macOS devices | Yes | Yes |
| Device discovery | No | Yes |
| Device inventory | No | Yes |
| Vulnerability management capabilities | No | Yes |
| Threat Analytics | No | Yes |
| Automated Investigation and Response | No | Yes |
| Advanced Hunting | No | Yes |
| Endpoint Detection and Response | No | Yes |
| Microsoft Threat Experts | No | Yes |
| Support for Windows (client and server) and non-Windows platforms (macOS, iOS, Android, and Linux) | No | Yes |
As you might have noticed, Defender for Endpoint Plan 2 offers all features and capabilities included in Plan 1, along with an additional set of capabilities exclusive to Plan 2.
Plan 2 also offers the option of purchasing the Defender Vulnerability Management add-on to further reduce your cybersecurity risk.
Defender Vulnerability Management add-on for Plan 2
Defender Vulnerability Management is a solution offered for identifying, assessing, remediating, and tracking vulnerabilities across your most critical assets. The add-on service helps your security and IT team by providing features such as:
- Security baseline assessment: This helps you monitor the devices in your organization and assess them against industry security benchmarks.
- Block vulnerable applications: This allows your security team to temporarily block all known vulnerable versions on installed applications until remediation is complete
- Browser extensions assessment: This allows you to monitor all browser extensions installed across the different devices in your organization.
- Network share analysis: Identifies vulnerable network share configurations and provides actionable security recommendations.
Choosing whether you need Defender for Endpoint Plan 1, Defender for Endpoint Plan 2 and/or include Vulnerability Management Add-on can sound like a bit of a challenge. Especially because when it comes to cybersecurity products, you wouldn’t want to make a mistake.
You can reach out to Amaxra’s team of experienced cybersecurity experts if you need help with assessing and addressing the security needs of your organization and choosing the right plan.
Microsoft Advanced Threat Protection Pricing

Of course, before you go ahead and purchase any of the plans and add-ons, you would want to know more about Advanced Threat Protection pricing, so you can make a smart decision about which security product would be the best fit for your organization.
To begin with, both plans for Windows Defender Advanced Threat Protection are now available as standalone offerings, as well as a built-in feature of Microsoft 365. This is a welcome change, as earlier, only companies that purchased the more expensive E5 plan for Microsoft 365 would receive Defender for Endpoint as a built-in feature.
If you don’t want or need the full set of features offered by E5, you can purchase Defender for Endpoint as a standalone product, which will cost you $3 per user for Plan 1 and $5.20 per user for Plan 2.
This offers coverage of five devices per user, including all Macs, Windows 7, Windows 9.1, or Windows 10 devices, regardless of whether the users or the organization owns the devices.
This is a helpful consideration in a world increasingly moving towards remote working and bring-your-own-device policies!
Office 365 Advanced Threat Protection License Requirements
We’ve already mentioned that you can purchase both Plan 1 and Plan 2 as standalone products, but if you want to know which Microsoft plans include Windows Defender for Endpoint as a standalone product and which allow you to purchase them and add-ons, let’s take a quick look at this table:
| Microsoft Subscription Plan | Defender for Endpoint |
| Microsoft 365 E5 | Built-in |
| Microsoft 365 A5 | Built-in |
| Microsoft 365 Business Premium | Built-in |
| Exchange Online Plan 1 | Available as add-on |
| Exchange Online Plan 2 | Available as add-on |
| Exchange Online Kiosk | Available as add-on |
| Exchange Online Protection | Available as add-on |
| Microsoft 365 Business Basic | Available as add-on |
| Microsoft 365 Business Standard | Available as add-on |
| Microsoft 365 Enterprise E1 | Available as add-on |
| Microsoft 365 Enterprise E3 | Available as add-on |
| Microsoft 365 Enterprise F3 | Available as add-on |
| Microsoft 365 A1 | Available as add-on |
| Microsoft 365 A3 | Available as add-on |
Windows Defender Advanced Threat Protection (now known as Defender for Endpoint) also directly integrates with various other Microsoft solutions that your organization may be using on a daily basis, including:
- Microsoft Defender for Cloud
- Microsoft Sentinel
- Intune
- Microsoft Defender for Cloud Apps
- Microsoft Defender for Identity
- Microsoft Defender for Office
- Skype for Business
This means your entire Microsoft ecosystem will be protected with post-breach capabilities. However, if you want a security solution that integrates both pre and post-breach threat protection, you can choose to supplement Windows Advanced Threat Protection with other Microsoft security solutions.
(If you’re still confused or unable to decide, don’t worry. Our team of experts has a strong understanding of what solutions you need to achieve the coverage you need.)


Need Help with Microsoft Licensing?
Leave your Microsoft licensing, security, and software solutions to us so you can concentrate on moving your business forward.Drop Us a Line
Windows Defender Advanced Threat Protection FAQs

“What is Microsoft Defender for Endpoint?”
Microsoft Defender for Endpoint, formerly known as Windows Defender Advanced Threat Protection, is a post-breach cybersecurity solution that helps your organization monitor, detect, investigate and remediate advanced security threats. Defender for Endpoint leverages Microsoft’s analytics and research insights to identify and remediate threats that manage to get into your network through your anti-virus solution.
“How is Microsoft Defender for Endpoint (MSDE) different from Windows Defender?”
Windows Defender is a built-in product for the Windows 10 OS that provides antivirus and anti-malware capabilities, while Windows Defender is a post-breach solution designed to help organizations once their networks have been breached.
“What are the features of Microsoft Defender for Endpoint?”
Microsoft Defender for Endpoint offers an extensive set of features for protection against advanced threats, including attack surface reduction, endpoint detection and response, automated investigation and remediation, threat and vulnerability management, threat analytics, system security score, device control, and more.
“What are the benefits of Microsoft Defender for Endpoint?”
Microsoft Defender for Endpoint offers an additional layer of protection for your security ecosystem, protecting you against advanced threats. It provides post-breach capabilities that allow you to monitor the health of your network, be promptly alerted upon detection of suspicious activity, as well as investigate and remediate the threat.
Conclusion
Windows Defender Advanced Threat Protection, now known as Microsoft Defender for Endpoint, is a post-breach security solution for organizations operating on a zero-trust principle.
To keep your devices and network safe from cybersecurity threats, you must assume that there will be a cybersecurity attack and be prepared to respond to it.
With the sophisticated technology behind Defender Advanced Threat Protection, you can ensure that any harmful activity in your network does not go undetected.
It helps you be informed about any suspicious activities as soon as they occur and provides you with a rich set of data and insights to understand what the threat is and where it is going while also sharing recommended ways to remediate the threat.
If you want to know more about the features, benefits, pricing, and licensing requirements for Windows Defender Advanced Threat Protection and want to discuss whether it is the right fit for your business or not, waste no more time and get in touch with Amaxra’s experts here.


Get Started Today
We'll build a secure and complete Microsoft software solution for your business while you concentrate on what's important.
